We are facing vulnerable issues. Could you please help us resolve them? We have shared the screenshots for your reference
Please, we hope this issue will be resolved soon.
Hi @Asti,
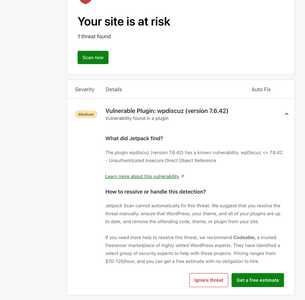
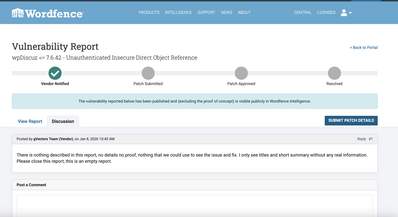
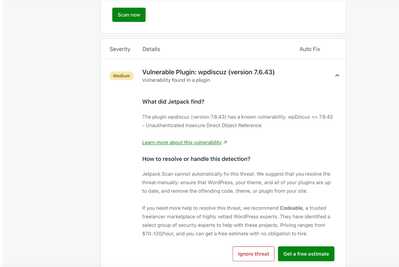
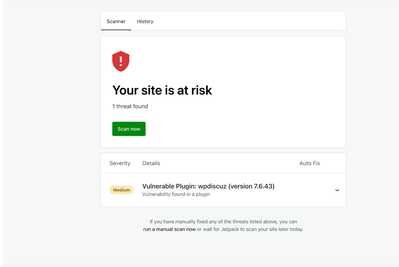
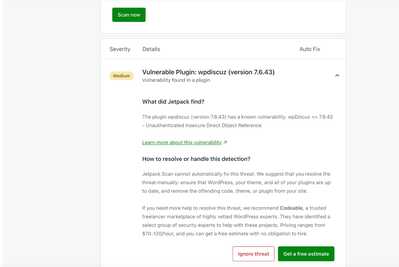
I second what @prabakaran reported. Wordfence flagged a vulnerability within the latest version of your plugin, V7.6.42.
Details:
1. Wordfence Screenshot: https://prnt.sc/nHIPb3vZtPWz
2. Wordfence Central: https://www.wordfence.com/threat-intel/vulnerabilities/wordpress-plugins/wpdiscuz/wpdiscuz-7642-unauthenticated-insecure-direct-object-reference
Also, the above was reported by another user one week ago as noted here: https://wordpress.org/support/topic/vulnerability-164/
Patch needed ASAP.
Thank you!
Bumping this to add on that it was also flagged by JetPack
This is not a false positive. The vulnerability is a classic IDOR in wpDiscuz AJAX actions exposed via admin-ajax.php. Below is a minimal proof of concept that worked on a default wpDiscuz installation without any custom modifications, prior to backend hardening.
Affected endpoint:
POST /wp-admin/admin-ajax.php
Example PoC (unauthenticated, no nonce):
curl -X POST https://example.com/wp-admin/admin-ajax.php \
-d "action=wpdVoteOnComment&commentId=1"
Observed behavior (pre-fix): Request is accepted without authentication No nonce validation is enforced
commentId is trusted directly from user input The action is executed or reaches application logic
This allows: Enumeration of commentId values
Mass voting / interaction with arbitrary comments
Bypassing frontend protections (CAPTCHA, rate limits, JS checks)
Abuse via direct HTTP requests without using the wpDiscuz UI
This is a textbook Insecure Direct Object Reference (IDOR) user-controlled object IDs are processed without authorization or ownership checks.
CAPTCHA and per-user limits are frontend-only and are bypassed entirely
High-traffic sites cannot distinguish this abuse from normal AJAX traffic
The issue is not theoretical — it is trivially exploitable with curl or any HTTP client
Mitigation (temporary, user-side): We mitigated this by enforcing backend validation:
Verifying nonce presence for sensitive wpd* actions
Validating that commentId / parentId / replyTo reference existing objects
This confirms the vulnerability exists at the application logic level.
If you need additional PoCs (e.g. subscription abuse, reply manipulation, or request logs), I can provide them. This report is not “about nothing” — it is about missing authorization checks on user-controlled object references.